The surge of unidentified drone sightings near U.S. military installations, both domestically and internationally, has ignited a wave of speculation and concern. Initially sparking curiosity online, the phenomenon has rapidly infiltrated mainstream political discourse, prompting investigations by law enforcement agencies and statements from high-ranking government officials. While authorities currently downplay any national security threat, the sheer number of sightings and their proximity to sensitive locations raise questions about the nature and intent of these aerial incursions. The ongoing investigation aims to unravel the mystery behind these drones, categorize their origin, and address any potential security risks they may pose.
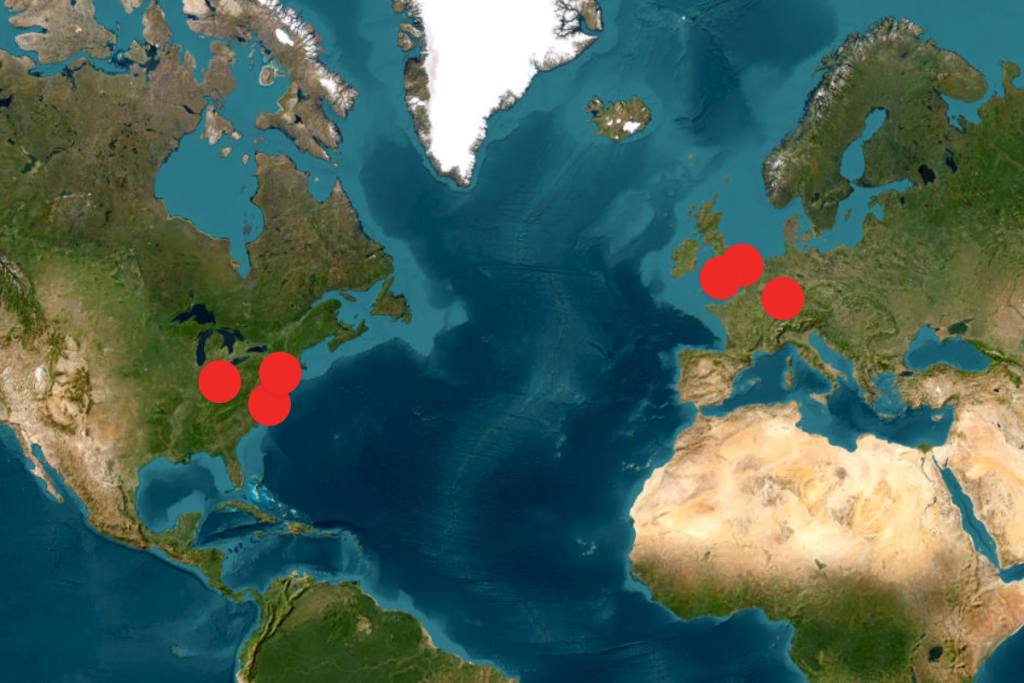
The drone sightings began last month in New Jersey, spreading to neighboring New York and Pennsylvania. Subsequently, reports emerged of drones near several key military installations across the U.S., including Picatinny Arsenal, Naval Weapons Station Earle, Wright-Patterson Air Force Base, and Langley Air Force Base. These locations, crucial for research, manufacturing, and strategic operations, raise the stakes of the drone incursions. Simultaneously, reports from the U.K. detailed similar activity near RAF Lakenheath, RAF Mildenhall, and RAF Feltwell, air bases utilized by the U.S. Air Force. Adding to the international scope of the phenomenon, unidentified drones were also reportedly observed over Ramstein Air Base in Germany, a vital U.S. airbase in Europe. The widespread nature of these sightings, spanning multiple countries and impacting key military infrastructure, underscores the need for a thorough and comprehensive investigation.
The response from government officials and agencies has been a mixture of reassurance and cautious monitoring. President Biden, while acknowledging the sightings, downplayed the potential for malicious intent, suggesting they might be authorized or hobbyist drones. However, former President Trump took a more forceful stance, demanding transparency and advocating for shooting down unidentified drones. Federal agencies, including the FBI, Department of Homeland Security, FAA, and Department of Defense, issued a joint statement asserting no immediate national security threat. They attributed the sightings to a combination of legal commercial and hobbyist drones, law enforcement activity, and even misidentified celestial objects. The FBI, having received thousands of tips related to the drone activity, continues to investigate, aiming to identify any potential patterns or connections between the various incidents.
The current investigation faces the complex task of sifting through numerous reports, differentiating between legitimate drone activity and potentially unauthorized or even hostile operations. Determining the origin and purpose of these drones is paramount. Are they advanced technological probes by foreign adversaries, coordinated efforts by domestic groups, or simply the result of increased drone usage coinciding with heightened awareness and reporting? The investigation must address these questions to accurately assess the risk and formulate appropriate responses. Differentiating between commercial, hobbyist, law enforcement, and potentially malicious drones requires sophisticated tracking and identification technologies, as well as close coordination between various agencies.
The drone incidents raise several crucial questions about security protocols surrounding sensitive installations. Are current measures adequate to detect and deter unauthorized drone activity? What steps can be taken to enhance surveillance and protection of these vital locations? The ongoing investigation may lead to a reassessment of existing security measures and the implementation of new technologies or strategies to address this emerging threat. In addition to physical security, the investigation also needs to consider the potential for cyberattacks or electronic warfare related to these drone incursions. Could these drones be used for reconnaissance, jamming communications, or even delivering payloads? Addressing these possibilities requires a comprehensive approach that integrates cybersecurity and physical security measures.
The continuing investigation into these drone sightings will likely focus on several key areas. Firstly, identifying the operators of the drones and determining their motives is crucial. This may involve analyzing flight patterns, tracking drone registrations, and potentially intercepting communications. Secondly, assessing the capabilities of these drones and their potential threat level is essential. This includes analyzing any sensor data collected by the drones, examining their payload capacity, and evaluating their potential for disruption or attack. Thirdly, strengthening security protocols around critical infrastructure and military bases is a priority. This may involve deploying counter-drone technology, implementing stricter airspace regulations, and enhancing surveillance capabilities. The outcome of this investigation will significantly impact future drone regulations, security measures, and the ongoing debate about balancing privacy and national security in an era of increasingly sophisticated unmanned aerial technology.